Electronic Team uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our cookie policy. Click here to learn more.

All data transmissions are encrypted using the TLS 1.2 protocol, ensuring your information remains inaccessible to unauthorized individuals.

We enforce end-to-end encryption and route your data through the minimum number of channels and points to ensure its privacy and security.

Our servers are hosted in Akamai clouds for maximum flexibility, security, and resilience in case problems occur.
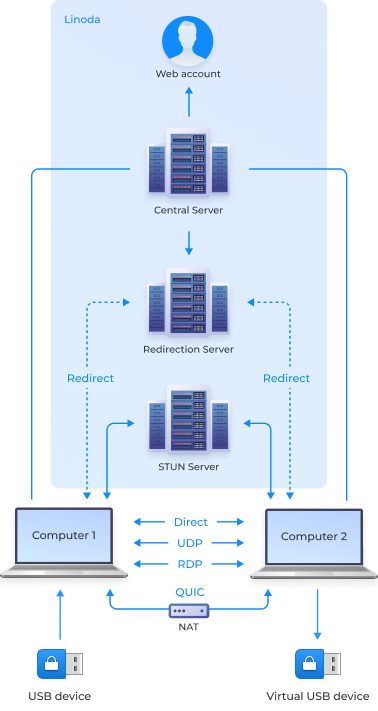
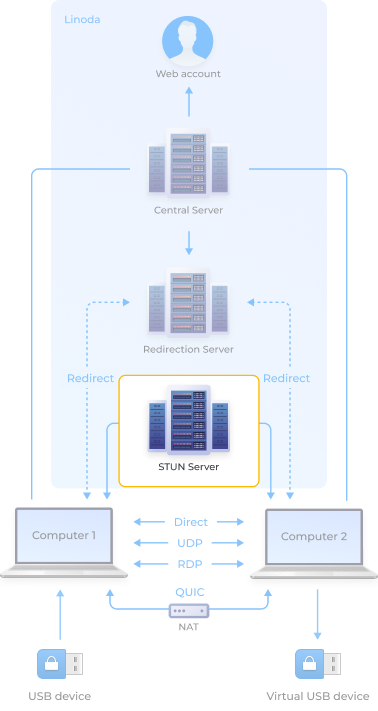
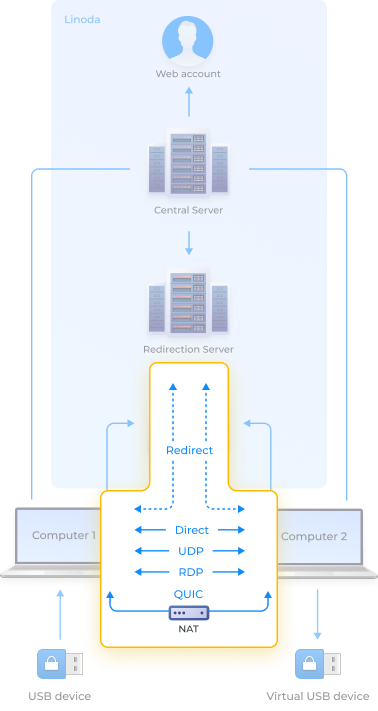
A direct, point-to-point connection offers the fastest data transmission speed by eliminating go-betweens and directly transferring data between two computers.
QUICPriority #2This connection method bypasses potential NAT issues by encapsulating data and establishing a UDP tunnel for stable connectivity.
UDPPriority #3This method also utilizes a point-to-point connection between two computers. It is less stable than a direct connection, but can be used to establish communication when creating a direct path with TSP is not possible.
RDPPriority #4This technique uses the Microsoft RDP channel to transfer data directly between two computers.
RedirectPriority #5This method uses a repeater to connect any two machines with Internet access. It has a low bandwidth due to the repeater and is the only type of connection that transmits device data.