Electronic Team uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our cookie policy. Click here to learn more.
Developing software is an expensive endeavor. It often requires years of research and development before it can go to market and start generating an income. Software companies therefore must engage in active protection of their software to prevent theft of their intellectual property and their potential earnings. Protecting your software against forgeries also protects your company's image and brand as dodgy software that may resemble your own could reflect badly as the end user may associate it with yours.
Software protection encompasses the premeditated actions taken to protect the software from all forms of piracy and theft. These actions can follow a legal route, or it can harness the power of available technology. Some of these measures are discussed in greater detail later in this article.
Software Piracy involves the illegal sharing and distribution of software. This can be intentional or incidental, for example - a simple act of sharing a single user license with a family member can constitute piracy.
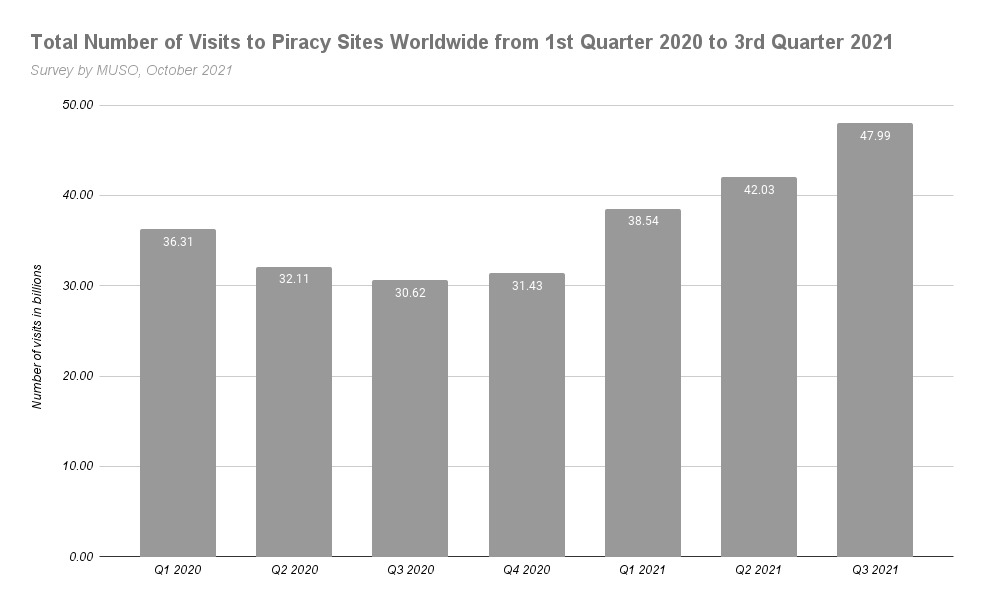
There are many popular torrent websites available. Torrents, while not necessarily illegal, often have a bad connotation as the contents that are being downloaded are not monitored. A torrent is a peer to peer file sharing system and illegal or cracked software is often shared on these platforms Torrent sites enjoy wide popularity. Studies by MUSO show that from early 2020 to Q3 2021, the number of users visiting torrent sites are in the billions and still on the increase.
Software piracy can be divided into these 5 categories.
While it is often said that imitation is the highest form of flattery, it's never a pleasant feeling having your idea stolen- especially if you are trying to earn an income from it. Forgery encompasses copying an existing product with the intention of deception and pretending that it is the genuine item. This can often infringe on copyright laws as well.
Internet Piracy includes the likes of Torrent sites. Users are able to upload and share copyrighted software using unauthorized channels. Software distributed on these channels are often counterfeit.
This form of piracy is the most common amongst general users. This can take the form of unauthorized copying of software; the sharing of passwords and products serial numbers; or outright lying about the user type I.e claiming to be a student for a discounted subscription fee.
Happens when there are a large number of users all using the same copy of a particular software application concurrently.
You may unknowingly find yourself purchasing a computer that has illegal or cracked software installed. An unscrupulous seller may do this so that they can push up the resale price. You as the end user may either unwittingly be using illegal software, or you may find the software to be glitchy, and you won’t be able to upgrade your software and you definitely won't receive and product support when you need it.
There are a number of ways for a company or a developer to protect their software and intellectual property. The most obvious and immediate thing to implement is a non-disclosure agreement (NDA). Everyone working with the software should sign a NDA to ensure that confidential information is not leaked in any way.
It is also important to determine ownership of intellectual property and code at the onset. An IP assignment agreement states that all work produced during the term of employment belongs to the company. This will ensure that should any employee take the existing code to a competitor, they would be in breach of the IPA and legal action can be taken against them.
Always make use of legal avenues available to you in your region. Copyrights and trademarks are legally binding and enforceable by law.
Copyright protects any original work or product from being copied. Copyright can also pertain to parts of your product, it does not have to be the whole product.
A Trademark applies mostly to designs, slogans and logos or symbols that help to identify a brand of a company. By registering a trademark, any design or slogan that bears a resemblance to your trademarked one can be legally required to change it to avoid any confusion or deception.
Anything that may be deemed as a unique selling point (USP) should be patented. A patent protects your inventions and prohibits anyone from copying or attempting to distribute or manufacture your product or a product that is deemed similar.
A dongle is a convenient and portable way to protect your software. The USB stick or dongle must be inserted into the computer to authenticate the user license. In order for this to work, the software sends a verification request to the I/O port to which the dongle is inserted. This is often done at startup of the software application and again at regular intervals. This ensures that the dongle is not simply shared between multiple users.
The software will expect a validation code in response to its requests. If this fails, the application can then respond accordingly, either by shutting down or restricting the functions available to the user.
Dongles make use of public-private keys. The encryption keys are stored safely in the flash drive. Some dongles are able to connect to a network - thereby allowing them access to a licence server. The software can request a license from the flash drive or the license server. As an added level of security, it is possible to link a license specifically to the hardware on a particular computer. This binding can be against the CPU, hard drive etc. This means that even if a dongle is found, it can not be simply inserted into any computer and used.
A dongle may not provide 100% protection against software piracy but it does provide some degree of protection as it is not an easy process to try and copy a dongle.
There may be times when your company needs to share a dongle. This can be done legally using the Donglify app. Donglify lets you access security dongles legally over your network. This is especially useful when you have remote users who may only need access to the software occasionally. With Donglify, they do not need a physical dongle permanently. A company with a large workforce also does not need to invest in multiple dongles.

Other benefits to using Donglify include:
Encryption is a way of protecting data using a key and algorithm to produce encrypted output. By encrypting all your code, you make it harder for anyone trying to reverse engineer your applications thereby protecting your intellectual property.
Now that you have a better understanding of what options are available, you can implement a robust and reliable security system to protect your software.
In the same way that you'd allow your software to check for updates, so you should allow security updates to happen. This includes regular license checks with reminders to users of license expiration with an easy channel to renew etc.