Electronic Team uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our cookie policy. Click here to learn more.
There’s one issue that most users will report when it comes to implementing USB security tokens. That problem has to do with experiencing the full functionality of a device in scenarios where a physical connection isn’t an option.
Specific troubles can arise when users attempt to share access to a remote USB token via a network connection. For organizations relying on token-based authentification being shared amongst multiple users (like a bank token, for example), a dedicated 3rd-party tool that allows users to copy a device onto a remote computer is required.

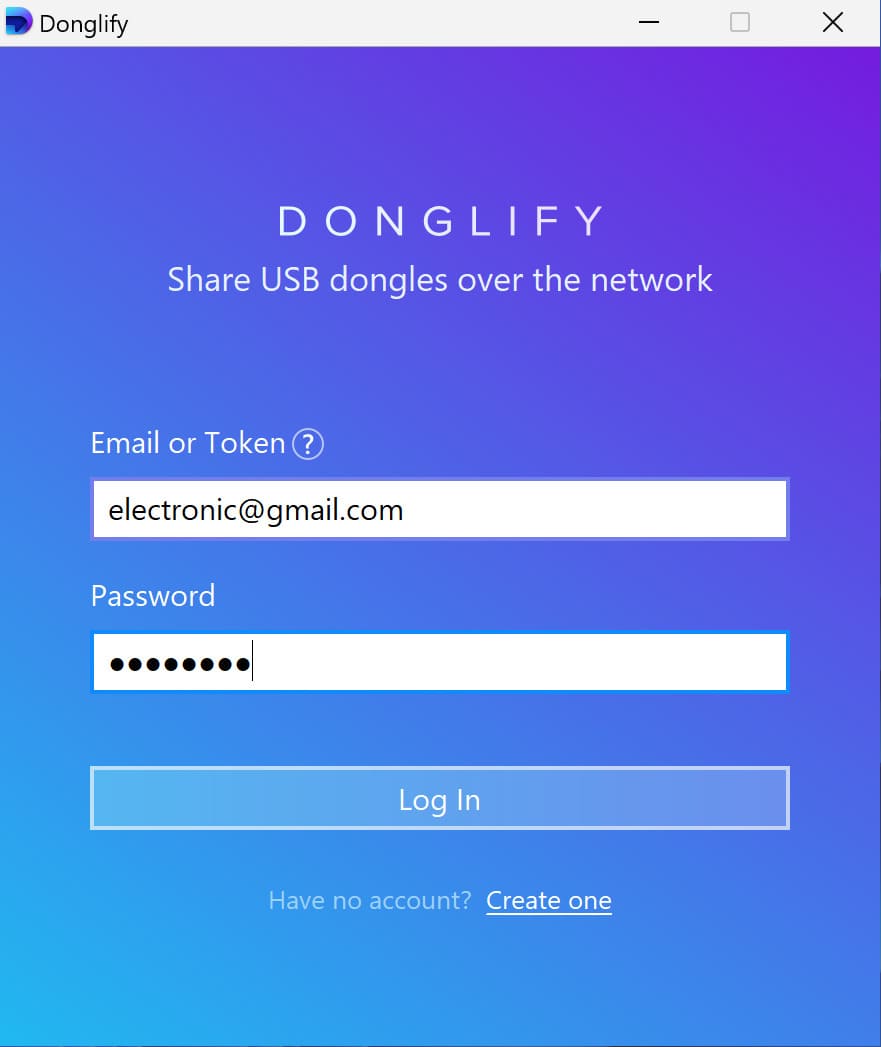
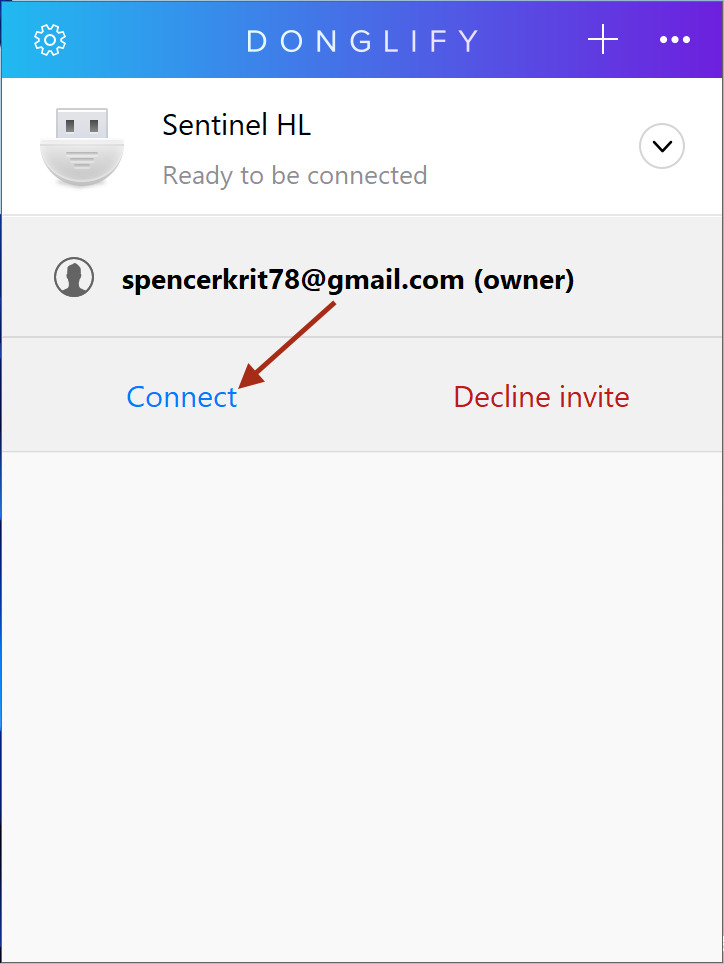
Here are several methods to share USB security tokens using a software solution:
There are two different ways that Donglify can be used:
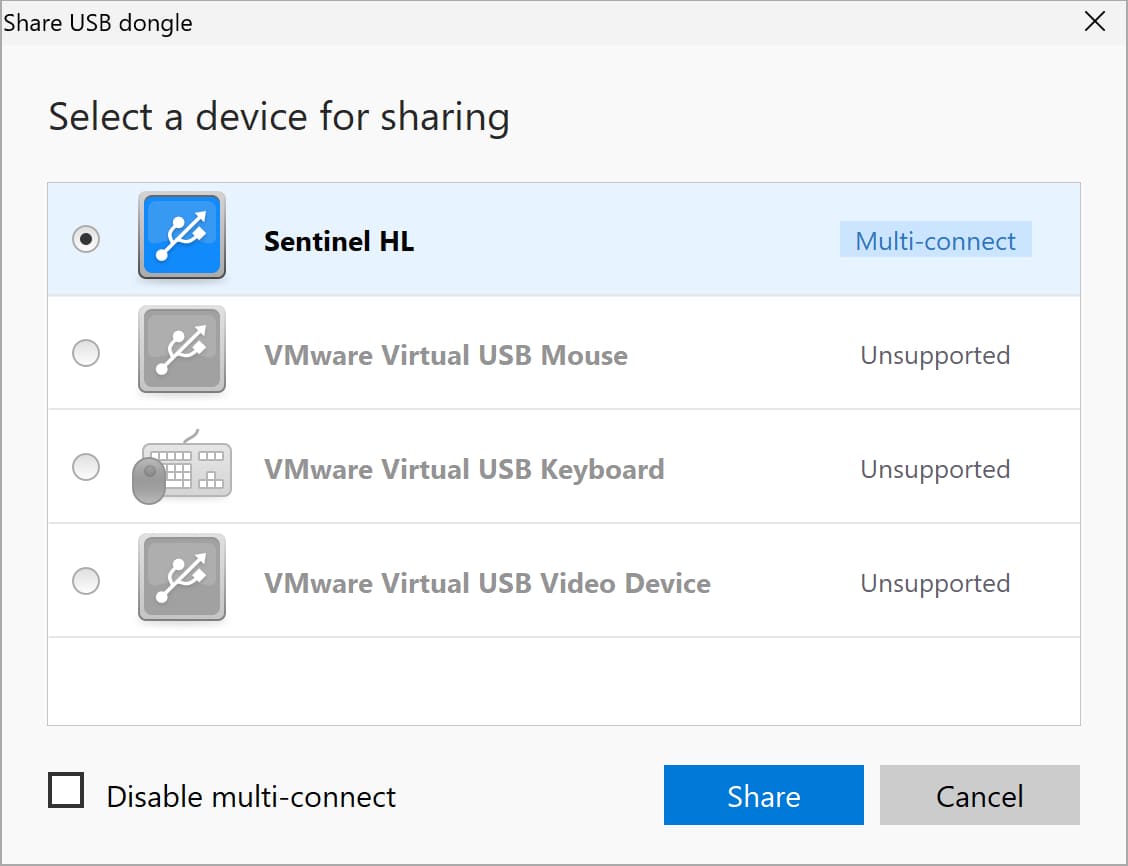
The tool can be used to access any type of USB security dongle from a single remote computer.
A multiconnect option is available that enables you to share a USB token over the network with multiple machines at the same time*.
After communication with the shared USB token is established, the device will be accessible through Device Manager just like it was physically connected to the machine. Donglify employs advanced encryption techniques to protect data transferred across the network, giving you peace of mind that your communication is secure.
FlexiHub is another software with features similar to those of Donglify. You can use it as remote access token software, but the tool does not offer the ability to establish multiple connections with the same device.
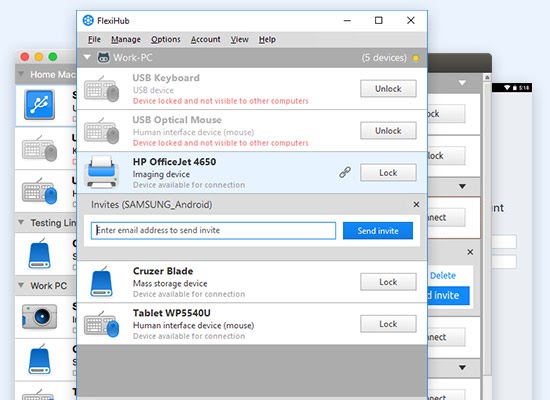
Follow these easy steps to use FlexiHub:
USB Network Gate enables you to access a security token with one remote machine at a time. A nice feature of the software is the ability to see which machine is currently connected to a USB device. This can be very useful if you have forgotten to disconnect the dongle from another computer.
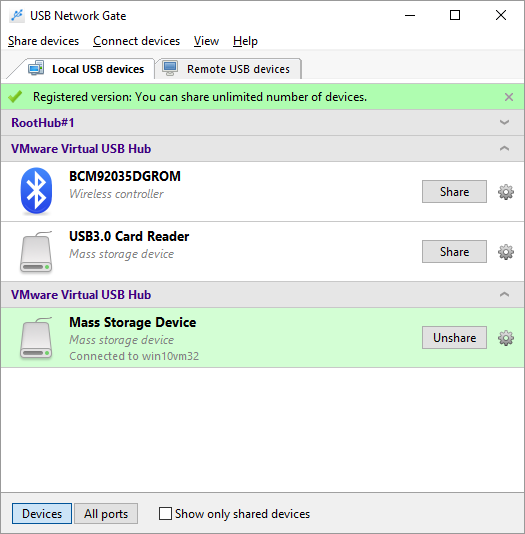
Here’s how to easily access a remote USB token using USB Network Gate: